Syllabus e-safety : Différence entre versions
(→=) |
(→CHAPTER 2 SYLLABUS - Privacy and data management) |
||
| (24 révisions intermédiaires par 2 utilisateurs non affichées) | |||
| Ligne 3 : | Ligne 3 : | ||
== Introduction : aims & resources == | == Introduction : aims & resources == | ||
| + | |||
| + | === Criteria, which are important by developing e-GUARDIAN questions === | ||
| + | |||
| + | •There should be two types of questions: | ||
| + | |||
| + | • question with four answers, of which one is correct, | ||
| + | • question with image (hotspot questions), where answer could be marked in the picture. | ||
| + | |||
| + | •It is important to create four questions for each syllabus item | ||
| + | |||
| + | •It is advisable to create equal length answers (for example, if there would be three long answers and one short, which is correct, test taker could have a clue about correct answer) | ||
| + | |||
| + | •It is advisable not to use specific software in the questions (exceptions may be possible, the information about this software must be in the educational material). | ||
| + | |||
| + | --[[Utilisateur:Donarena|Renata (Lithuania Team)]] 20 juin 2011 à 07:47 (UTC) | ||
=== Aims === | === Aims === | ||
| + | |||
This wiki page aims at facilitating a collaborative synergic process for defining the syllabus on netsafety of the EU LdV e-Guardian project. | This wiki page aims at facilitating a collaborative synergic process for defining the syllabus on netsafety of the EU LdV e-Guardian project. | ||
Participants are delegates of partner's institutions from Lithuania, Latvia, Germany and Switzerland. | Participants are delegates of partner's institutions from Lithuania, Latvia, Germany and Switzerland. | ||
| Ligne 50 : | Ligne 66 : | ||
=== Mind mapping for the key-notions of the syllabus === | === Mind mapping for the key-notions of the syllabus === | ||
| − | |||
| − | |||
In addition, Rémi Levy from APTES has produced a [http://www.mindomo.com/view.htm?m=0a1258e0720347bab585be7ac0e7baea mind mapping image] to represent all the notions for the e-safety syllabus. You can access to [http://www.mindomo.com/view.htm?m=0a1258e0720347bab585be7ac0e7baea the interactive map] - You can modify it directly because we keep a copy of the precedent contribution. | In addition, Rémi Levy from APTES has produced a [http://www.mindomo.com/view.htm?m=0a1258e0720347bab585be7ac0e7baea mind mapping image] to represent all the notions for the e-safety syllabus. You can access to [http://www.mindomo.com/view.htm?m=0a1258e0720347bab585be7ac0e7baea the interactive map] - You can modify it directly because we keep a copy of the precedent contribution. | ||
| Ligne 60 : | Ligne 74 : | ||
== CHAPTER 1 SYLLABUS - Basic knowledge on e-safety == | == CHAPTER 1 SYLLABUS - Basic knowledge on e-safety == | ||
| − | |||
| − | |||
| + | <span style="color:#FF0000">NOTICE IT IS BETTER IF COMMENTS AND DISCUSSIONS ARE MADE ON THE DISCUSSION PAGE </span> | ||
| − | + | <span style="color:#FF0000">New Syllabus version discussed on Thursday 16th June --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 08:28 (UTC) | |
| − | 1. | + | 1.1. Understand the differences of information [[contents]] (open, private, business, etc.). |
| − | 1. | + | 1.2. Be aware of '''[[privacy protection]] legal act''' (be aware of the responsibility for own actions on the Internet: when publishing, writing comments, downloading,etc) |
| − | 1. | + | 1.3. Know about '''[[equity between opportunities & risks]]''' of [[web2]] |
| − | 1. | + | 1.4. Understand the notion of '''[[identity]]'''. |
| − | 1. | + | 1.5. Be aware of '''different identity for authorization theft methods''' (skimming, pretexting, shoulder surfing, information diving). |
| − | 1.7. Be aware of cyber crime, online predators, financial scams, | + | 1.6. Know about '''[[social engineering]]''' and its methods. |
| + | |||
| + | 1.7. Be aware of cyber crime, online predators, financial scams, harms and who to contact when discovering illegal data. | ||
1.8. Understand computer infection threats (viruses, Trojan horses, spyware, dishonest adware, etc.). Know when and how malicious software can get into computer system. | 1.8. Understand computer infection threats (viruses, Trojan horses, spyware, dishonest adware, etc.). Know when and how malicious software can get into computer system. | ||
| − | 1.9. Know about organizational security: school security, usage of school web pages, content publishing, access, etc. | + | 1.9. Know about organizational [[security]]: school security, usage of school web pages, content publishing, access, etc. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | 1. | + | 1.10. Know about '''[[netiquette]] and other basic codes''' of conduct in the cyberspace (RFC 1855) |
| − | 1. | + | 1.11. Understand what is [[Online Safety 3.0]] and why [[digital citizenship]] is protective. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== CHAPTER 2 SYLLABUS - Privacy and data management == | == CHAPTER 2 SYLLABUS - Privacy and data management == | ||
| − | <span style="color:#FF0000">New Syllabus version | + | <span style="color:#FF0000">New Syllabus version discussed on Thursday 16th June </span> --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 08:35 (UTC) |
| − | |||
| − | |||
| − | 2. | + | 2.1. [[Distinguish between data and information]]. |
| − | 2. | + | 2.2. Understand the opportunities and risks of digital '''[[data management]]''' from fully collaborative to full privacy. |
| − | 2. | + | 2.3. Know about multi-layer '''[[password]]''', changing and keeping password policies. |
| − | 2. | + | 2.4. Know about '''safe computer [[login]] methods''' |
| − | 2. | + | 2.5. Know why to use multiple user accounts (#or password ? --[[Utilisateur:Remilevy|Rémi LEVY]] 24 juin 2011 à 13:46 (UTC)) on various digital environments. Understand the meaning and importance of access rights (what a personal user account is and how data of different users is separated). |
| − | 2. | + | 2.6. Be aware of '''data encryption''', decryption and password protected files. |
| − | 2. | + | 2.7. Understand what [[intellectual property]] on Internet is. |
| − | + | 2.8. Understand the benefits and purpose of data '''backups''' and be able to restore lost data. | |
| + | == CHAPTER 3 SYLLABUS - Security tools and network security == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <span style="color:#FF0000">New Syllabus version discussed on Thursday 16th June --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 09:24 (UTC) | |
| − | + | 3.1. Know computer '''network types''' : local area network (LAN), wide area network (WAN), virtual private network (VPN) and why protection is needed. | |
| − | + | 3.2. Know different network '''connection methods''' (Cable, Wireless, Mobile networks). | |
| − | |||
| − | 2 | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
3.3. Be able to use wireless network safe and know how to connect to a protected/unprotected wireless network. | 3.3. Be able to use wireless network safe and know how to connect to a protected/unprotected wireless network. | ||
| − | 3.4. Sharing and accessing resources over network ( | + | 3.4. '''Sharing and accessing resources''' over a network (files, printer, desktop). |
| − | 3.5. Understand safety means of computer networks ( | + | 3.5. Understand safety means of computer networks (airewall, antivirus, anti-spyware, spam blocker, password protection, connection encryption – wireless). |
3.6. Be able to use standard OS integrated protection tools. | 3.6. Be able to use standard OS integrated protection tools. | ||
| Ligne 183 : | Ligne 141 : | ||
3.7. Be able to turn on / off and adjust protection level in standard security means that are integrated in the operating system (Firewall, Protection tools, etc.). Distinguish different modes of antivirus protection (active, passive). | 3.7. Be able to turn on / off and adjust protection level in standard security means that are integrated in the operating system (Firewall, Protection tools, etc.). Distinguish different modes of antivirus protection (active, passive). | ||
| − | 3.8. Know what has to be done and in what order, if you suspect that computer system is infected. Distinguish infected files deletion, quarantining and curing. | + | 3.8. Know what has to be done and in what order, if you suspect that your computer system is infected. Distinguish between infected files deletion, quarantining and curing. |
| − | 3.9. Know how to follow, download and use updates for your operating system, software and importance of antivirus definition files. Understand the benefits of these updates. | + | 3.9. Know how to '''follow, download and use updates for your operating system''', software and importance of antivirus definition files. Understand the benefits of these updates. |
| + | |||
| + | 3.10. Be able to run informal and formal periodic [[external checkup]]. | ||
| − | |||
</span> | </span> | ||
| − | + | == CHAPTER 4 SYLLABUS - Minors and newcomers on the net == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | New Syllabus version | + | New Syllabus version discussed on Thursday 16th June - --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 08:53 (UTC) |
| − | |||
| − | 4.1. Understand the impact of communication with new users about safety in IT World. | + | 4.1. Understand the impact of communication with minors and new users about safety in IT World. |
| − | 4.2 | + | 4.2 Understand the purpose of monitoring, filtering and controlling tools for safer internet use of minors |
| − | 4.3. Be aware of different ways to | + | 4.3. Be aware of different ways to educate, monitor and control usage of social networking and other web sites. |
4.4. Be able to develop policies and applicate methods for children’s use of the computer and the Internet (depending on age and socio-cultural situation). | 4.4. Be able to develop policies and applicate methods for children’s use of the computer and the Internet (depending on age and socio-cultural situation). | ||
| − | 4.5.Understanding advantages and limitations | + | 4.5. Understanding advantages and limitations with protection software |
| − | |||
</span> | </span> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== CHAPTER 5 SYLLABUS - Social networks and safe usage of the Internet == | == CHAPTER 5 SYLLABUS - Social networks and safe usage of the Internet == | ||
| + | New Syllabus version as discussed on Thursday 16th June --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 09:05 (UTC) - | ||
| − | |||
| − | + | 5.1. Know how to '''start and finish safe browsing session''' (https, lock icon, always logout and close the browser window). Know consequences of unsafe browsing. | |
| − | + | 5.2. Know about'''advantages, disadvantages and dangers of Internet cookies''' and ActiveX control. Know about tools that ensure safety when browsing the Internet. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | 5.2. Know about advantages, disadvantages and dangers of Internet cookies and ActiveX control. Know about tools that ensure safety when browsing the Internet. | ||
5.3. Be able to manage: temporary Internet files, browser history, passwords, cookies and autocomplete data. | 5.3. Be able to manage: temporary Internet files, browser history, passwords, cookies and autocomplete data. | ||
| − | 5.4. Be able to safely connect to e-Services and secure | + | 5.4. Be able to safely '''connect to e-Services and secure environments'''– connecting and using, recover lost passwords. |
| − | 5.5. Know when and in which cases personal information can be published on the Internet (i.e. status publishing about leaving home). | + | 5.5. Know when and in which cases personal '''information can be published on the Internet''' (i.e. status publishing about leaving home). |
5.6. Know who you should contact if you discovered inappropriate information about you or your related digital identities. | 5.6. Know who you should contact if you discovered inappropriate information about you or your related digital identities. | ||
| − | 5.7. Understand that | + | 5.7. Understand that it is necessary to exercise critical thinking about content and identities on the internet. (i.e. blogs, Wikipedia, social networks, forums, etc). #reformulated by --[[Utilisateur:Remilevy|Rémi LEVY]] 17 juin 2011 à 09:22 (UTC) |
5.8. Understand 'threats of inappropriate content for different groups of people (duality of personality, psychological harm, racism, religious sect, alluring to buy something or disclose your information, information about drugs, violence and so on) | 5.8. Understand 'threats of inappropriate content for different groups of people (duality of personality, psychological harm, racism, religious sect, alluring to buy something or disclose your information, information about drugs, violence and so on) | ||
| − | 5.9. Understand what | + | 5.9. Understand what an online social network is, what are opportunities and risks of social network. Age groups of using social networks. Options and parameters for information disclosure. Understand what is the fascination to disclose private information on the internet |
| − | 5.10. Know different social network types (Friendship-driven and Interest-driven) and be able to use them harmless and safe (appropriate account privacy settings). | + | 5.10. Know different '''social network types''' (Friendship-driven and Interest-driven) and be able to use them harmless and safe (appropriate account privacy settings). |
5.11. Know what type of information recommended to be published on social network, be responsible for published content, and know impacts | 5.11. Know what type of information recommended to be published on social network, be responsible for published content, and know impacts | ||
| Ligne 290 : | Ligne 199 : | ||
5.14. Be aware of safe instant messaging. Understand confidentiality while using IM like: file sharing, non-disclosure of important information, etc. | 5.14. Be aware of safe instant messaging. Understand confidentiality while using IM like: file sharing, non-disclosure of important information, etc. | ||
| − | 5.15. Understand threats of | + | 5.15. Understand threats of online communication: virtual dating, bullying, commenting. |
5.16. Understand dependency and addiction to the Internet. | 5.16. Understand dependency and addiction to the Internet. | ||
| − | |||
| − | |||
| − | |||
| − | + | </span> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Another Mind mapping= | =Another Mind mapping= | ||
Version actuelle datée du 24 juin 2011 à 15:46
e-GUARDIAN - Syllabus V.2.x
Sommaire
- 1 Introduction : aims & resources
- 2 Other possible structure of the syllabus - A.P.T.E.S proposition
- 3 CHAPTER 1 SYLLABUS - Basic knowledge on e-safety
- 4 CHAPTER 2 SYLLABUS - Privacy and data management
- 5 CHAPTER 3 SYLLABUS - Security tools and network security
- 6 CHAPTER 4 SYLLABUS - Minors and newcomers on the net
- 7 CHAPTER 5 SYLLABUS - Social networks and safe usage of the Internet
- 8 Another Mind mapping
Introduction : aims & resources[modifier]
Criteria, which are important by developing e-GUARDIAN questions[modifier]
•There should be two types of questions:
• question with four answers, of which one is correct, • question with image (hotspot questions), where answer could be marked in the picture.
•It is important to create four questions for each syllabus item
•It is advisable to create equal length answers (for example, if there would be three long answers and one short, which is correct, test taker could have a clue about correct answer)
•It is advisable not to use specific software in the questions (exceptions may be possible, the information about this software must be in the educational material).
--Renata (Lithuania Team) 20 juin 2011 à 07:47 (UTC)
Aims[modifier]
This wiki page aims at facilitating a collaborative synergic process for defining the syllabus on netsafety of the EU LdV e-Guardian project. Participants are delegates of partner's institutions from Lithuania, Latvia, Germany and Switzerland.
The resources are :
A web-based social bookmarking working group[modifier]
on here on Diigo, we can post all related useful information on netsafety, such as :
- definition of key-words
- examples of quizz, pedagogical scenarios and other pedagogical resources
- related scientific articles
- other relevant initiatives
Guidelines for the syllabus[modifier]
They wwere provided by the project's team coordinated by the LIA organisation, and specially the syllabus workpackage leader, ecdl.lt, represented by Eugenijus Telesius and his team composed of Renata Danieliene & Tomas Lygutas, which is complemented by partner's delegate Algimantas Merkys (LIA, the coordinator's team), Dennis Krannich (Bremen Univbersity), Théo Bondolfi & Rémi Lévy (APTES Switzerland).
These guidelines are :
1. Focus on e-safety offline as well as online, therefore always taking into account basic needs (such as password storage) as well as complex needs (such as behaviour in web2 environments).
2. Taking into account all key-points in this initial version, and considering these key-point as "objects" whcih can be replaced in other forms but which must stay available.
3. respecting the steps of user point of view (example : 1 start computer, 2 launch application...)
4. restructuring with categories and sets like in the policies of ECDL [1]
5. keeping as much as possible the existing phrases and formulations, only changing (merging, repositioning, pionderating) when it suits the next step of test/scenarios
6. Keeping in mind the final intention of equity between risks & opportunities proposing positive practices (opportunities, in an educative perspective) and preventing bad practices (risks, which creates fear), based on the vision of the slide 10 of this presentation of Anne Collier, which says that netsafety3.0 should be :
- research-based, not fearbased, therefore relevant
- flexible & layered, instead of "one-size-fits-all"
- respectful of learning culture : stakeholders in positive experience, not just potential victims
- positive, empowering : not just safety from, but safety for...
- full, constructive engagement in participatory society (that's the context of the construction of this syllabus)
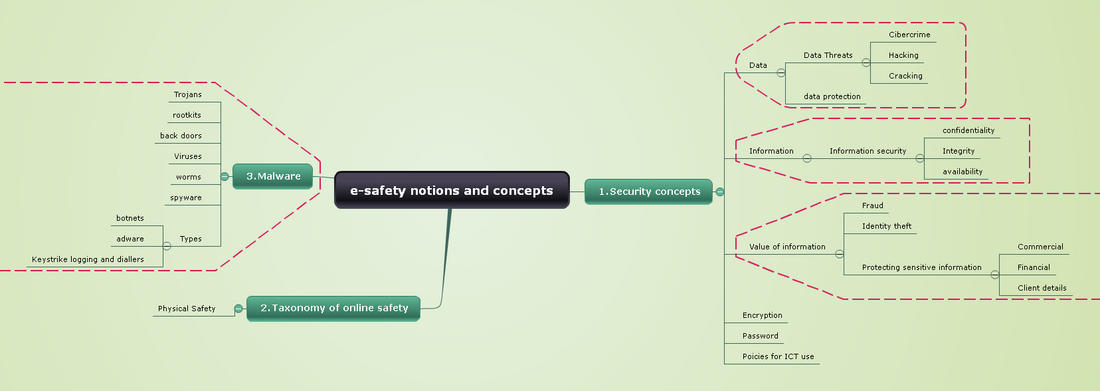
Mind mapping for the key-notions of the syllabus[modifier]
In addition, Rémi Levy from APTES has produced a mind mapping image to represent all the notions for the e-safety syllabus. You can access to the interactive map - You can modify it directly because we keep a copy of the precedent contribution.
Other possible structure of the syllabus - A.P.T.E.S proposition[modifier]
CHAPTER 1 SYLLABUS - Basic knowledge on e-safety[modifier]
NOTICE IT IS BETTER IF COMMENTS AND DISCUSSIONS ARE MADE ON THE DISCUSSION PAGE
New Syllabus version discussed on Thursday 16th June --Rémi LEVY 17 juin 2011 à 08:28 (UTC)
1.1. Understand the differences of information contents (open, private, business, etc.).
1.2. Be aware of privacy protection legal act (be aware of the responsibility for own actions on the Internet: when publishing, writing comments, downloading,etc)
1.3. Know about equity between opportunities & risks of web2
1.4. Understand the notion of identity.
1.5. Be aware of different identity for authorization theft methods (skimming, pretexting, shoulder surfing, information diving).
1.6. Know about social engineering and its methods.
1.7. Be aware of cyber crime, online predators, financial scams, harms and who to contact when discovering illegal data.
1.8. Understand computer infection threats (viruses, Trojan horses, spyware, dishonest adware, etc.). Know when and how malicious software can get into computer system.
1.9. Know about organizational security: school security, usage of school web pages, content publishing, access, etc.
1.10. Know about netiquette and other basic codes of conduct in the cyberspace (RFC 1855)
1.11. Understand what is Online Safety 3.0 and why digital citizenship is protective.
CHAPTER 2 SYLLABUS - Privacy and data management[modifier]
New Syllabus version discussed on Thursday 16th June --Rémi LEVY 17 juin 2011 à 08:35 (UTC)
2.1. Distinguish between data and information.
2.2. Understand the opportunities and risks of digital data management from fully collaborative to full privacy.
2.3. Know about multi-layer password, changing and keeping password policies.
2.4. Know about safe computer login methods
2.5. Know why to use multiple user accounts (#or password ? --Rémi LEVY 24 juin 2011 à 13:46 (UTC)) on various digital environments. Understand the meaning and importance of access rights (what a personal user account is and how data of different users is separated).
2.6. Be aware of data encryption, decryption and password protected files.
2.7. Understand what intellectual property on Internet is.
2.8. Understand the benefits and purpose of data backups and be able to restore lost data.
CHAPTER 3 SYLLABUS - Security tools and network security[modifier]
New Syllabus version discussed on Thursday 16th June --Rémi LEVY 17 juin 2011 à 09:24 (UTC)
3.1. Know computer network types : local area network (LAN), wide area network (WAN), virtual private network (VPN) and why protection is needed.
3.2. Know different network connection methods (Cable, Wireless, Mobile networks).
3.3. Be able to use wireless network safe and know how to connect to a protected/unprotected wireless network.
3.4. Sharing and accessing resources over a network (files, printer, desktop).
3.5. Understand safety means of computer networks (airewall, antivirus, anti-spyware, spam blocker, password protection, connection encryption – wireless).
3.6. Be able to use standard OS integrated protection tools.
3.7. Be able to turn on / off and adjust protection level in standard security means that are integrated in the operating system (Firewall, Protection tools, etc.). Distinguish different modes of antivirus protection (active, passive).
3.8. Know what has to be done and in what order, if you suspect that your computer system is infected. Distinguish between infected files deletion, quarantining and curing.
3.9. Know how to follow, download and use updates for your operating system, software and importance of antivirus definition files. Understand the benefits of these updates.
3.10. Be able to run informal and formal periodic external checkup.
CHAPTER 4 SYLLABUS - Minors and newcomers on the net[modifier]
New Syllabus version discussed on Thursday 16th June - --Rémi LEVY 17 juin 2011 à 08:53 (UTC)
4.1. Understand the impact of communication with minors and new users about safety in IT World.
4.2 Understand the purpose of monitoring, filtering and controlling tools for safer internet use of minors
4.3. Be aware of different ways to educate, monitor and control usage of social networking and other web sites.
4.4. Be able to develop policies and applicate methods for children’s use of the computer and the Internet (depending on age and socio-cultural situation).
4.5. Understanding advantages and limitations with protection software
CHAPTER 5 SYLLABUS - Social networks and safe usage of the Internet[modifier]
New Syllabus version as discussed on Thursday 16th June --Rémi LEVY 17 juin 2011 à 09:05 (UTC) -
5.1. Know how to start and finish safe browsing session (https, lock icon, always logout and close the browser window). Know consequences of unsafe browsing.
5.2. Know aboutadvantages, disadvantages and dangers of Internet cookies and ActiveX control. Know about tools that ensure safety when browsing the Internet.
5.3. Be able to manage: temporary Internet files, browser history, passwords, cookies and autocomplete data.
5.4. Be able to safely connect to e-Services and secure environments– connecting and using, recover lost passwords.
5.5. Know when and in which cases personal information can be published on the Internet (i.e. status publishing about leaving home).
5.6. Know who you should contact if you discovered inappropriate information about you or your related digital identities.
5.7. Understand that it is necessary to exercise critical thinking about content and identities on the internet. (i.e. blogs, Wikipedia, social networks, forums, etc). #reformulated by --Rémi LEVY 17 juin 2011 à 09:22 (UTC)
5.8. Understand 'threats of inappropriate content for different groups of people (duality of personality, psychological harm, racism, religious sect, alluring to buy something or disclose your information, information about drugs, violence and so on)
5.9. Understand what an online social network is, what are opportunities and risks of social network. Age groups of using social networks. Options and parameters for information disclosure. Understand what is the fascination to disclose private information on the internet
5.10. Know different social network types (Friendship-driven and Interest-driven) and be able to use them harmless and safe (appropriate account privacy settings).
5.11. Know what type of information recommended to be published on social network, be responsible for published content, and know impacts
5.12. Understand that online socializing reflects "real life".
5.13. Be able to send/receive e-mail securely: know how to reject email from specific email addresses. Know how to treat email messages from unknown senders, classified as spam and email messages infected with malware. Know about scam, hoax, chain letters.
5.14. Be aware of safe instant messaging. Understand confidentiality while using IM like: file sharing, non-disclosure of important information, etc.
5.15. Understand threats of online communication: virtual dating, bullying, commenting.
5.16. Understand dependency and addiction to the Internet.
</span>
Another Mind mapping[modifier]
You can access to the dynamic mapp here notions and concepts